Securing the Backbone: Electronic Access Control for Critical Infrastructure
/ Author: Matthias Gromann / Reading time: about 5 minutes
In the heart of our digital world, data centers hum with activity. Within their temperature-controlled cages and racks reside the unsung heroes - servers, storage arrays, and network equipment - forming the critical infrastructure that powers our online lives. These devices are not just important, they are mission-critical. Protecting them is paramount, not only from the ever-evolving threats of cybersecurity, but also from unauthorized physical access.
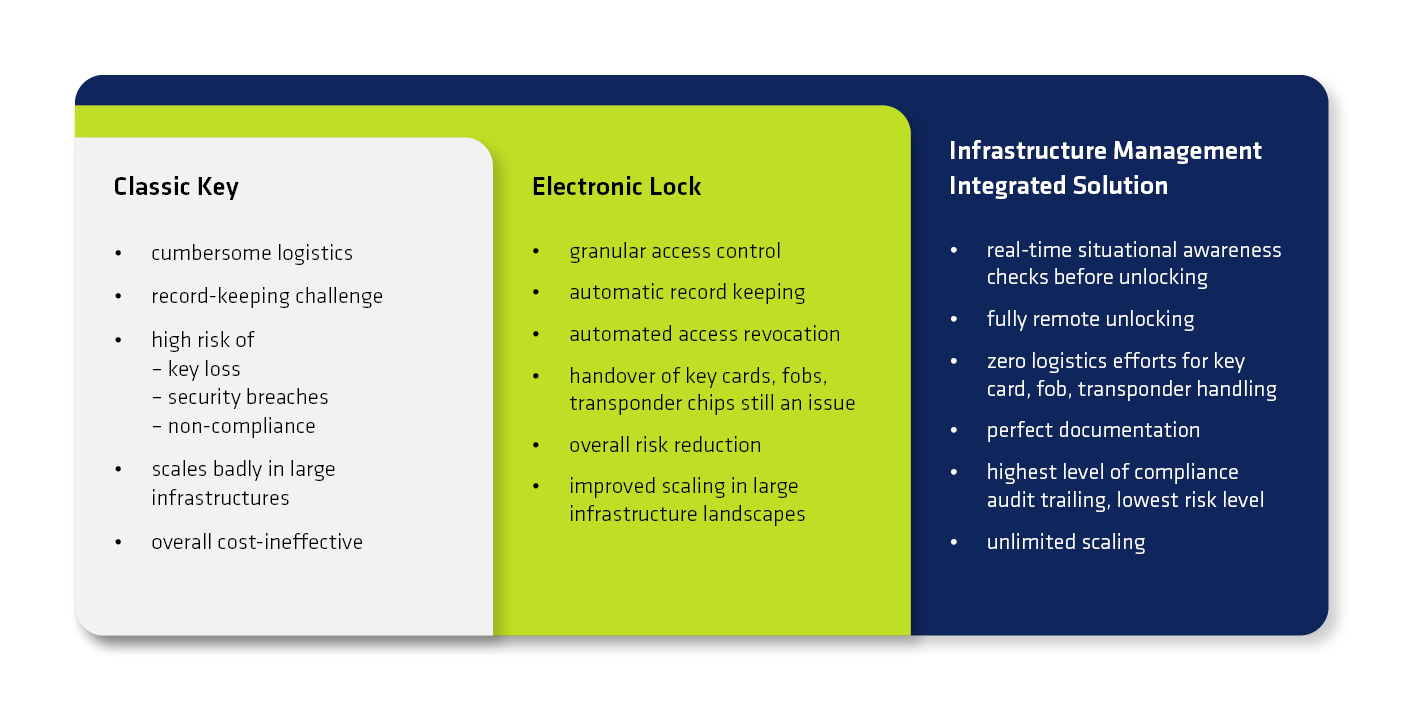
Traditional lock-and-key solutions, while seemingly straightforward, fall short when it comes to efficiently managing access control in data centers. Distributing keys can be a logistical nightmare, requiring meticulous record-keeping to ensure proper sign-off procedures are followed. The ever-present risk of lost keys poses a significant security breach, potentially jeopardizing compliance regulations and incurring hefty replacement costs.
Fortunately, the landscape of physical access control has evolved alongside the demands of our digital age. State-of-the-art electronic lock systems offer a comprehensive solution, streamlining access management while bolstering security.
Enhanced Security and Control:
- Granular Access Levels: Electronic systems allow for assigning individual access permissions to authorized personnel. This allows for granular control, restricting access based on specific needs. Think of it as a digital gatekeeper, granting entry only to those with the proper credentials.
- Audit Trails and Accountability: Every access attempt, successful or otherwise, is meticulously logged. These audit trails provide a clear picture of who accessed a particular rack at a specific time, fostering accountability and aiding in any potential security investigations.
- Integration with Existing Security Systems: Leading electronic lock systems seamlessly integrate with existing security infrastructure, such as CCTV cameras and alarm systems. This creates a centralized platform for monitoring and managing overall security posture. Companies like Kentix (https://kentix.com/en) offer integrated solutions that combine physical access control with environmental monitoring for a comprehensive security umbrella.
Operational Efficiency and Streamlined Access:
- Eliminating Lost Keys: Gone are the days of misplaced keys and frantic searches. Electronic systems utilize key cards, fobs, or transponder chips for access control. These methods are not only more convenient but also eliminate the security risks associated with lost physical keys.
- Automated Access Revocation: When an employee leaves the company or their role changes, their access privileges can be instantly revoked electronically. This eliminates the need to physically collect and deactivate keys, saving time and resources.
- Scalability and Adaptability: Electronic systems are inherently scalable, allowing for easy expansion as needs change. Adding new personnel or restricting access to specific areas becomes a matter of a few clicks within the user management interface.
In the realm of critical infrastructure management, even the sophisticated capabilities of electronic access control systems may prove insufficient to meet the stringent demands of certain scenarios if they are operated in an isolated fashion. Consider a large data center employing subcontractors for remote hands operations. The distribution of key cards, fobs, or transponder chips, while offering improvements over traditional keys, still introduces logistical complexities and security concerns, particularly with frequent personnel changes. These methods, though more controlled than physical keys, still necessitate physical handover and tracking, reintroducing some of the administrative burdens they were designed to alleviate.
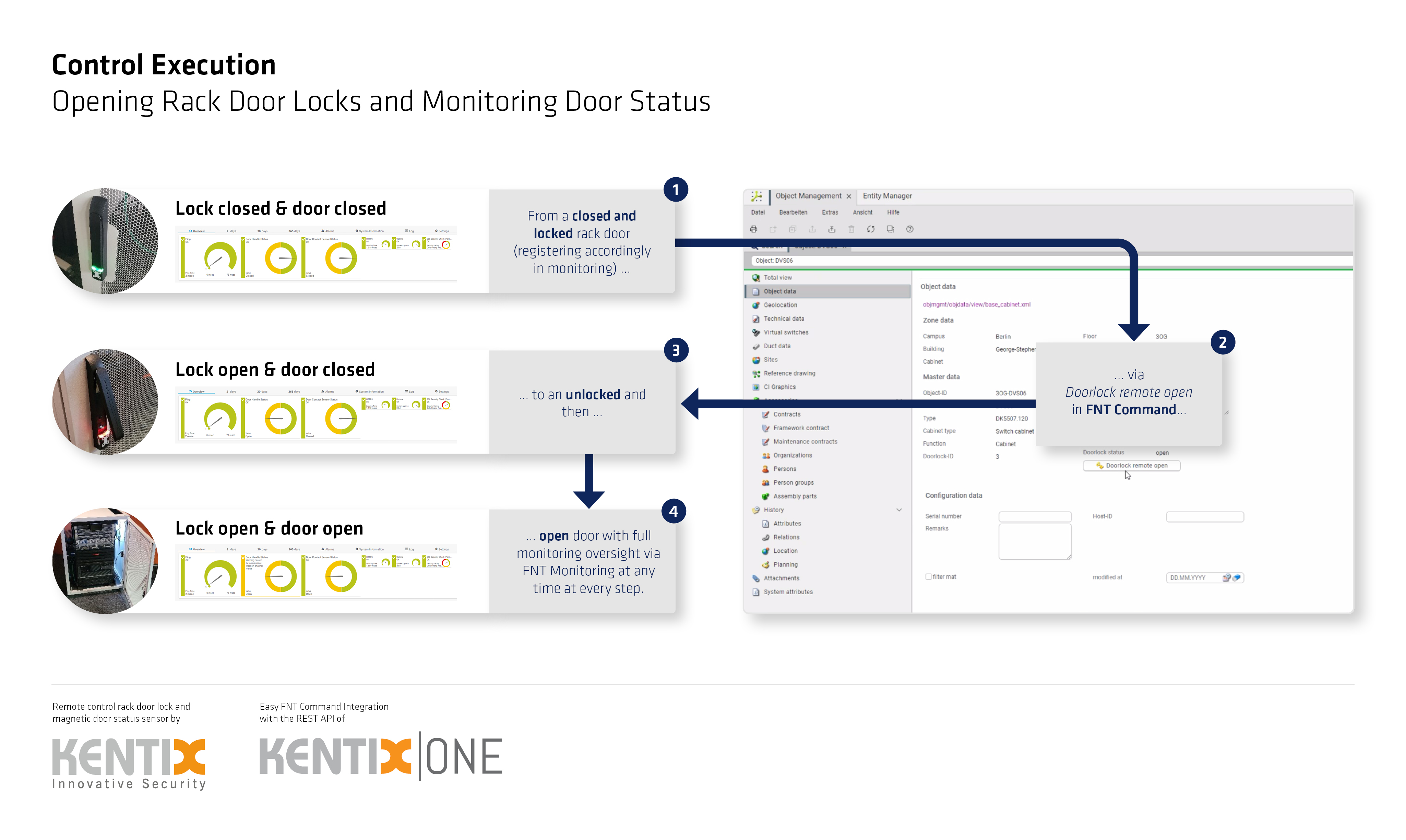
This is where the power of integrated IT/Data Center/Network infrastructure management solutions, such as FNT Command, truly shines. These platforms, acting as a comprehensive digital twin of the entire data center environment, offer a new paradigm in access control. Modern electronic lock solutions, equipped with network connectivity and API integration, can be seamlessly integrated into these management platforms. This integration enables remote control of every cage and rack door fitted with an electronic lock, granting authorized personnel the ability to grant or deny access on demand from a central management console.
The digital twin's inherent documentation capabilities provide an unprecedented level of real-time situational awareness. When an access request is received, the operator personnel in central control can instantly perform a cross-check, verifying critical information: What equipment resides within the target rack? Who are the designated owners of these devices? Which services and applications are hosted on them, and what is their criticality? Are any scheduled changes or maintenance activities planned that justify the requested access? Only after these crucial questions are answered – a process completed in mere moments – is the command to unlock the door issued, granting access.
This remote unlocking capability is itself subject to rigorous access control. Only individuals assigned to specific, vetted roles are granted the authority to perform such actions. For environments with exceptionally high security requirements, a two-person control principle can be implemented, requiring a secondary authorization from another employee or supervisor before unlocking can proceed. This adds an extra layer of security, mitigating the risk of unauthorized access even further.
Four Essential Key Takeaways:
- Enhanced Security and Streamlined Operations: Electronic access control systems offer granular access control, detailed audit trails, and integration with existing security systems. This combination strengthens security posture while simplifying access management and reducing administrative burdens.
- Eliminating Lost Credentials and Automated Revocation: Electronic access control eliminates the risk of lost physical keys and streamlines access revocation upon personnel changes. This saves time and resources while mitigating security risks associated with lost credentials.
- Scalability and Adaptability: Electronic systems are inherently scalable, allowing for easy adaptation to changing needs. Expanding access or adding new personnel becomes a simple task.
- Digital Twin Integration for Superior Control: Combining electronic locks with a comprehensive digital twin platform unlocks a new level of control. This empowers central management to grant or deny access on demand, perform real-time situational awareness checks, and enforce rigorous access control protocols for enhanced security in critical infrastructure settings.